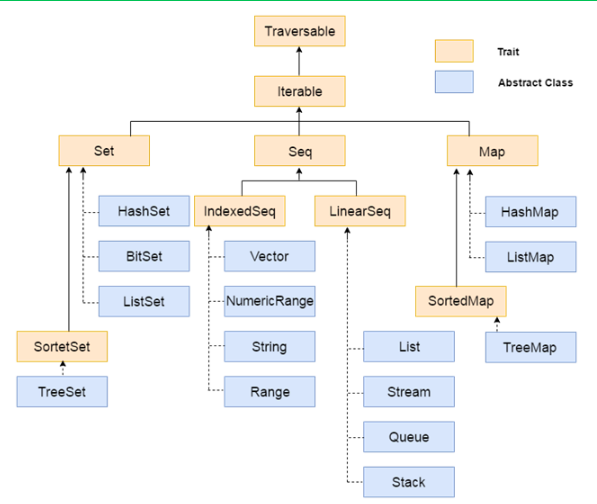
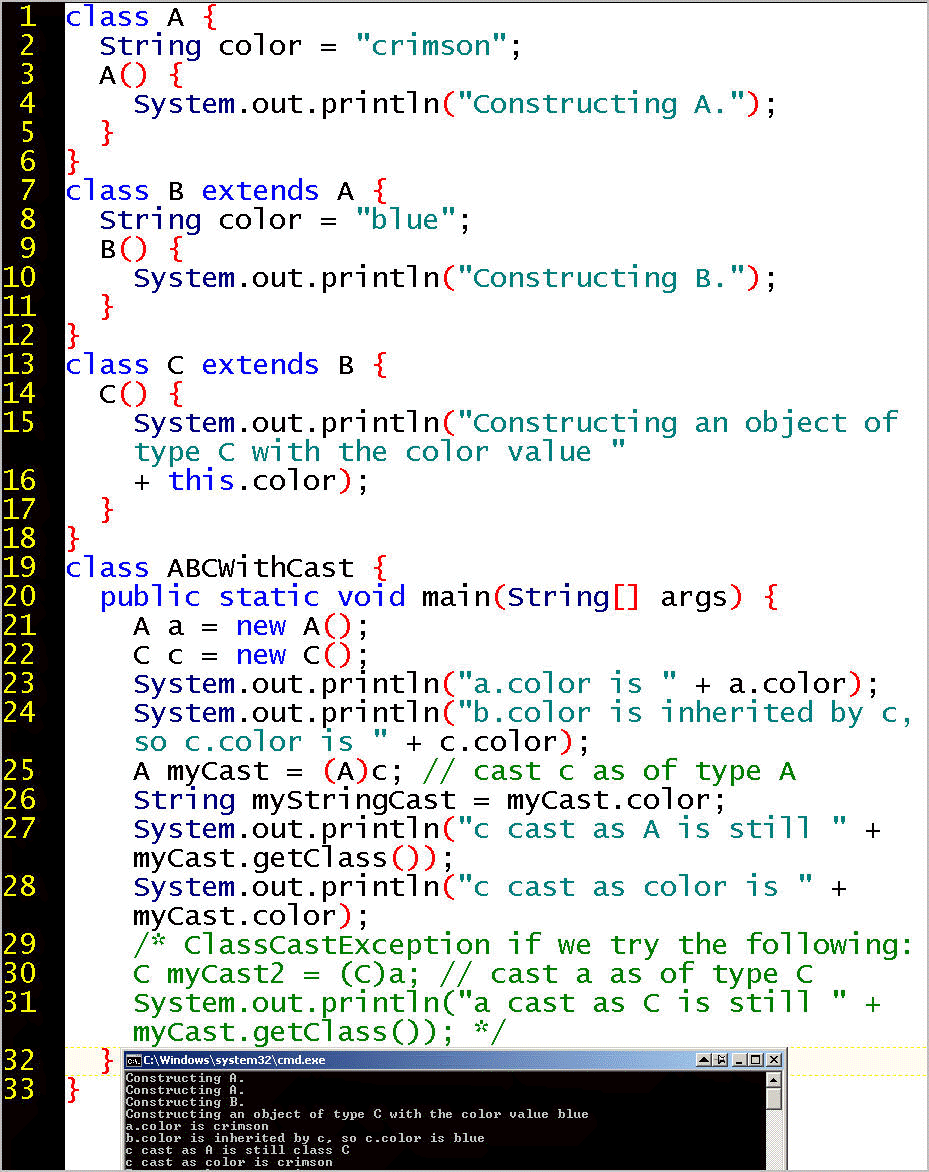
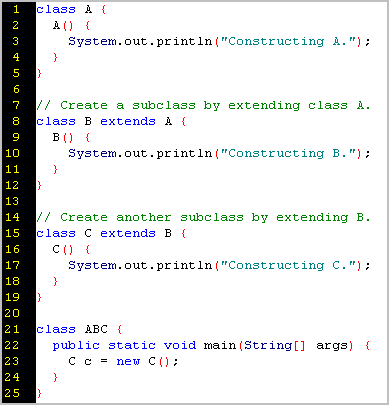
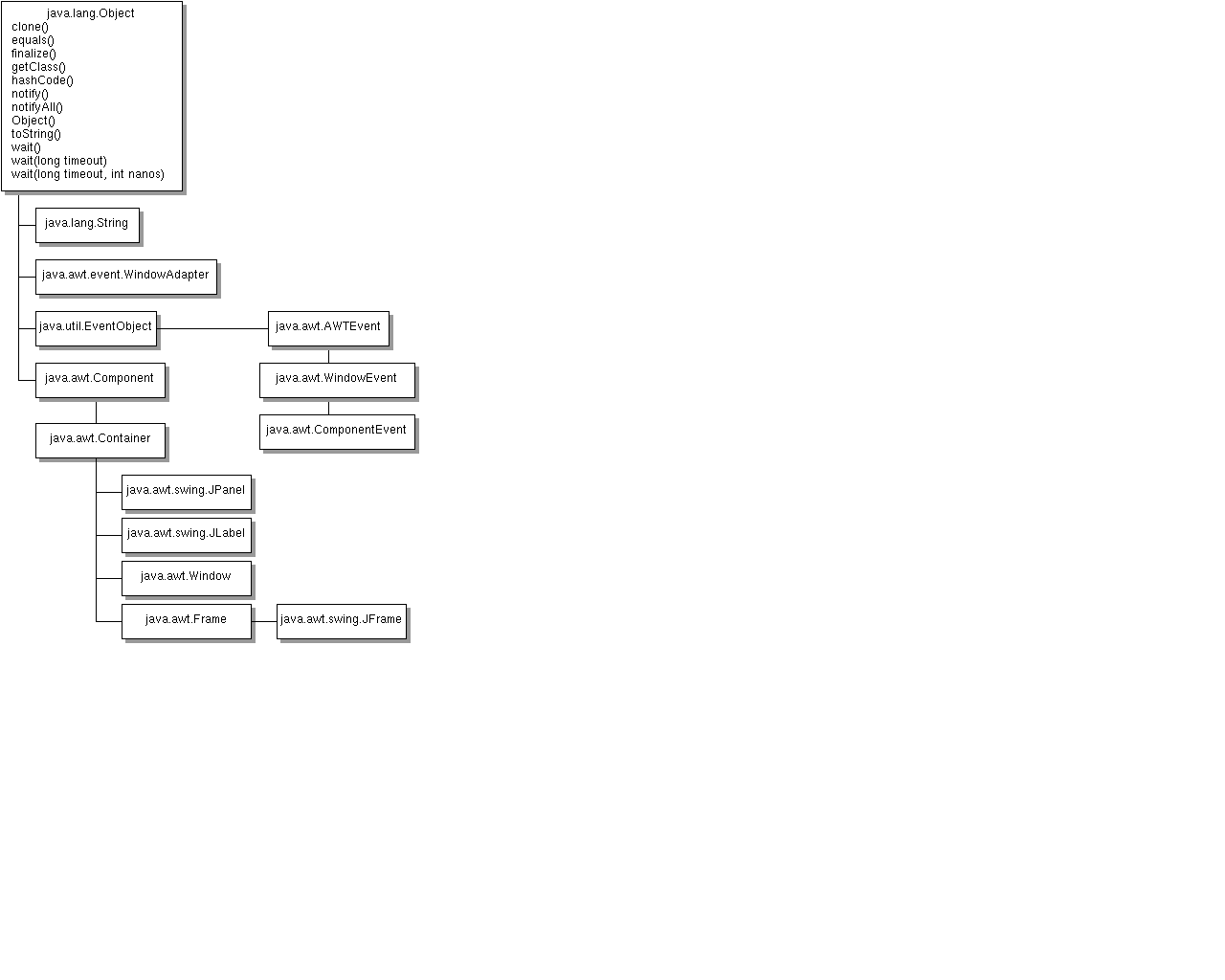
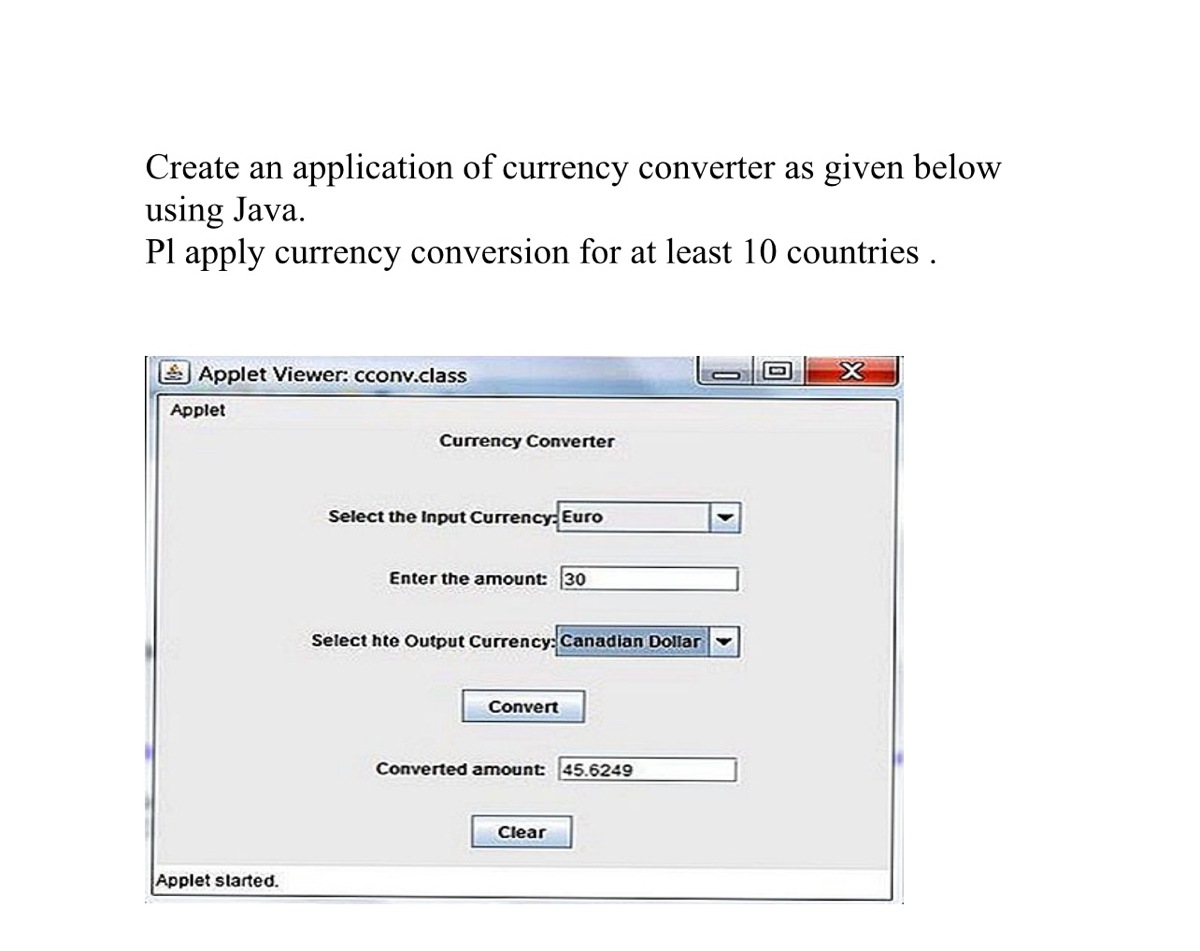
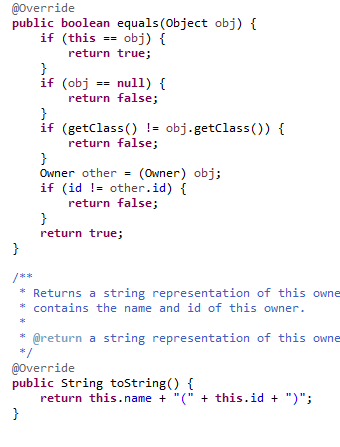
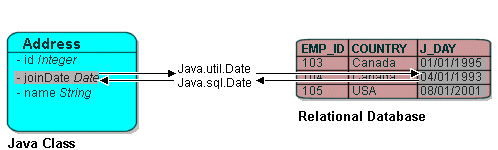
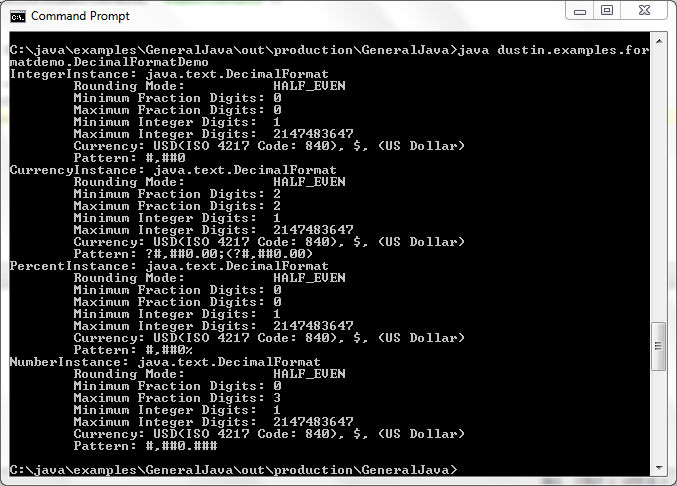
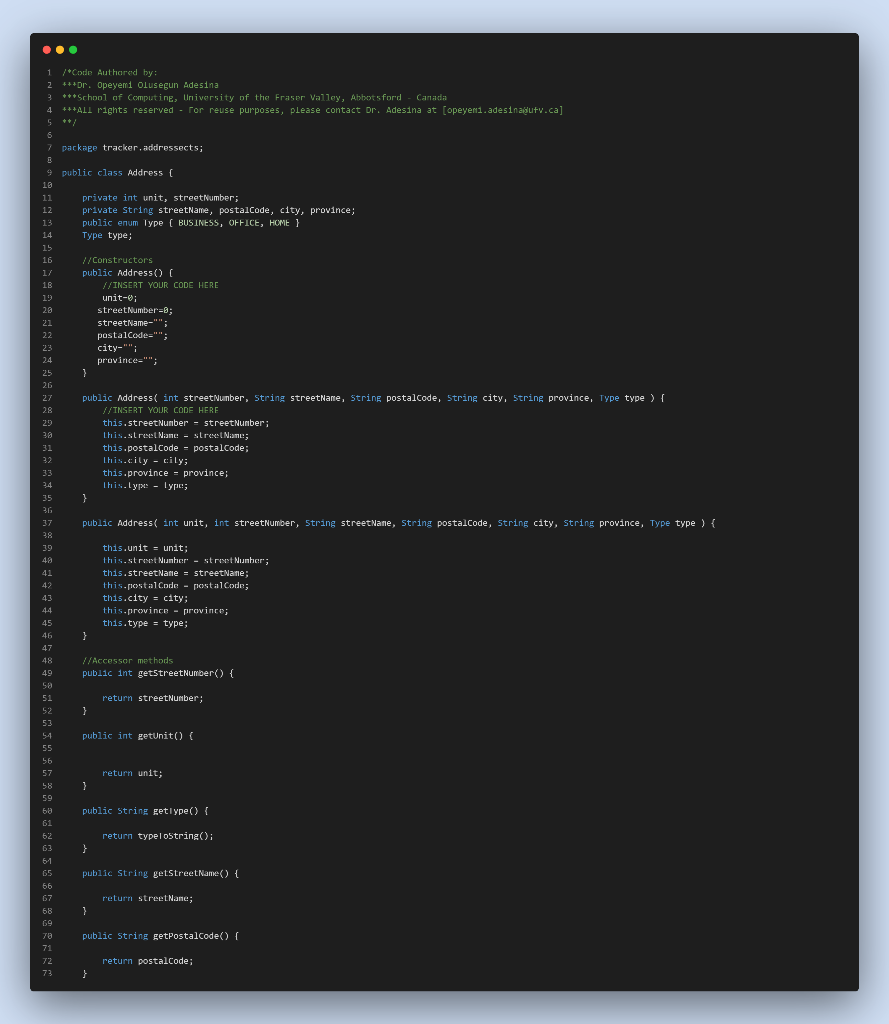
Entropy | Free Full-Text | KEADA: Identifying Key Classes in Software Systems Using Dynamic Analysis and Entropy-Based Metrics

Deprecated: Migrate traditional WebSphere apps to WebSphere Liberty on IBM Cloud Private by using Kubernetes - IBM Cloud Architecture Center

Symmetry | Free Full-Text | RIM4J: An Architecture for Language-Supported Runtime Measurement against Malicious Bytecode in Cloud Computing

java - Can I use a HashMap to pick which interface (DAO) to autowire in SpringBoot? - Stack Overflow

Symmetry | Free Full-Text | RIM4J: An Architecture for Language-Supported Runtime Measurement against Malicious Bytecode in Cloud Computing

Polymorphic bytecode instrumentation - Binder - 2016 - Software: Practice and Experience - Wiley Online Library

Symmetry | Free Full-Text | RIM4J: An Architecture for Language-Supported Runtime Measurement against Malicious Bytecode in Cloud Computing